Despite being made aware about the most popular scams that are occurring within our shores, smartphone users might still fall for scams – even if they do not engage in get rich schemes, or anything that promises low commitment and high returns.
Potential of these malwares
Most malware remains dormant in your phone – as it silently harvests data such as your contact list, incoming messages, photo gallery or your notes app. Some programs have misleading app icons that could be disguised as something else – such as a notes or photo gallery app.
Granting access to your contact lists and content gallery would give attackers the potential to extort you with the potential contents they find in your content gallery. Attackers might contact you through mediums such as WhatsApp (disguised with foreign numbers) and extort their victims by threatening to release sensitive content to their list of phone numbers.
It is terrifying to wonder what these syndicates could do – they might use your contacts and impersonate your identity to scam other victims as well. The list goes on.
Another prominent capability of these malicious apps are their screen and audio recording abilities, which grant malicious parties to observe sensitive information being typed on-screen, such as login credentials and usage habits.
New tactics that goes beyond stealing your information
Recently, a new type of malware has been brought to the attention of the public – those which obtain unauthorised access to the victims’ devices. A local victim was gradually promoted to install and grant relevant permissions to an app, as directed by an agent over the phone.
The victim gradually noticed that her apps started flickering and her “banking apps flashed up on the screen”. Immediate action was executed – she managed to shut down her phone and visited a branch for help.
Identifying as a tech literate, it goes to show how susceptible anyone could be – in terms of falling victim to the ever-evolving scam tactics.
How did it creep into your phone
Given that Android phones run on “community-based, open-source platform”, it is inevitable that more than half of the local phone users (based on local market share statistics) would be more vulnerable to such threats.
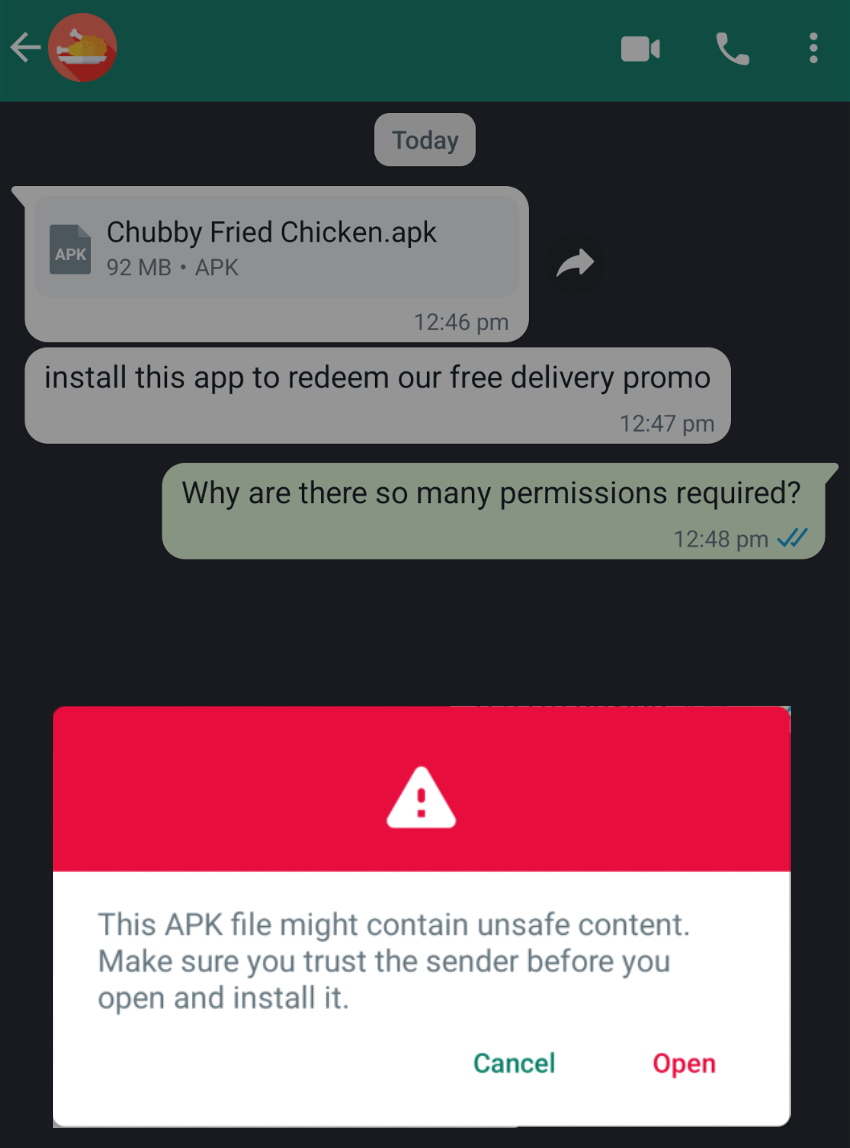
Even if you are not a firm believer of investment campaigns, these apps can still show up in different forms – such as through eBook, movies, manga apps. Websites offering such content might prompt content aficionados to install their apps for easy content viewing.
Signs and symptoms
On most phones, having additional malware in the background could mean a surge in overheating and increased battery consumption. This could be a good indication especially if you have already tried terminating your background apps and you used to have optimal battery life.
Some phones might also display an indicator at the top of the screen when sensitive permissions (such as camera, microphone, location service, screen recording, etc.) are currently being utilised. These could be a telltale sign that you are being remotely monitored.
Failsafe mechanisms in place
Depending on the financial application you are using, apps such as OCBC mobile banking will not run when such applications are detected on your phone. Most financial apps will prompt you to update your software to the latest iteration before you can conduct any transactions.
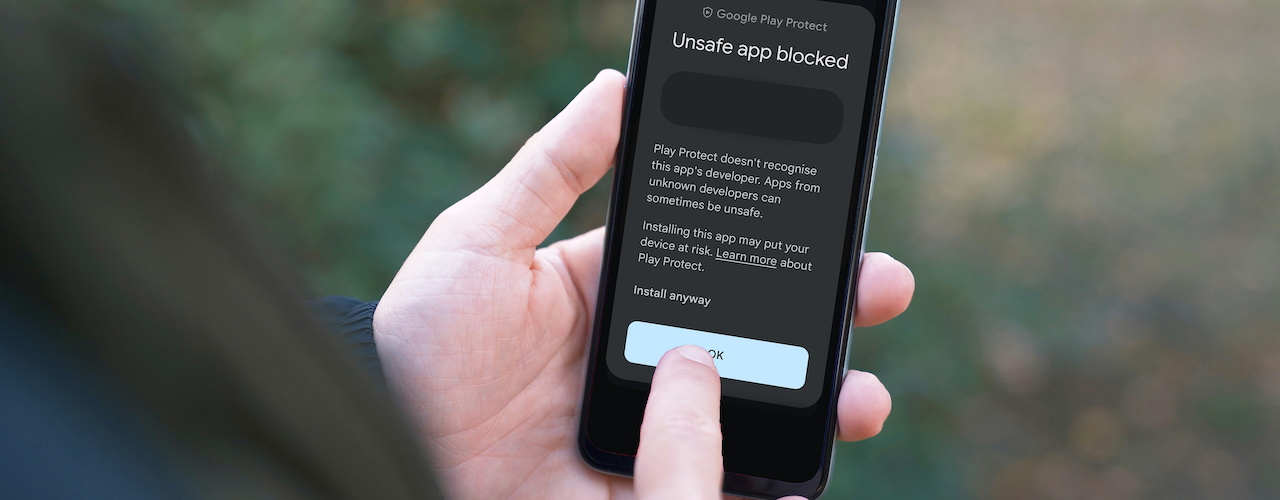
Upon installation of suspicious applications, most (up-to-date) Android editions will be equipped to halt installations to request for a second confirmation – users can only continue the process after they forgo the warnings.
Users obsessed with cleaning their phone’s system should be reassured that modern smartphones are already able to optimise itself without any third-party apps. If absolutely necessary, stick to offerings from major developers such as Google or Norton.
Just a side note – these “phone cleaning” apps could also be malware themselves and hoard system resources, especially since they can run in the background.
Staying vigilant – by being discerning
Unless you are a current or prospective iPhone user – which is, currently, a less popular target for malware-related scams, the tips that will be mentioned are likely to prevent your smartphone from being compromised.
We start off with checking permissions – the beginning of every malware infiltration attempt.
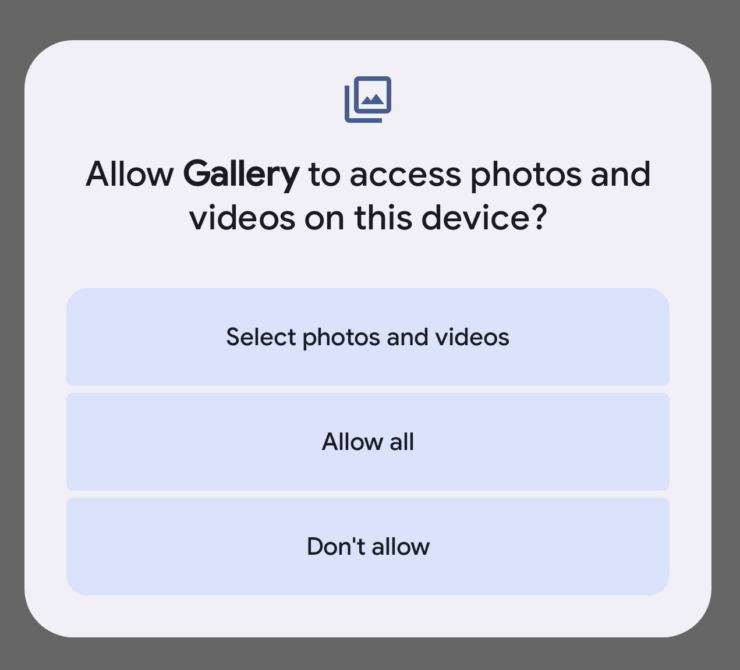
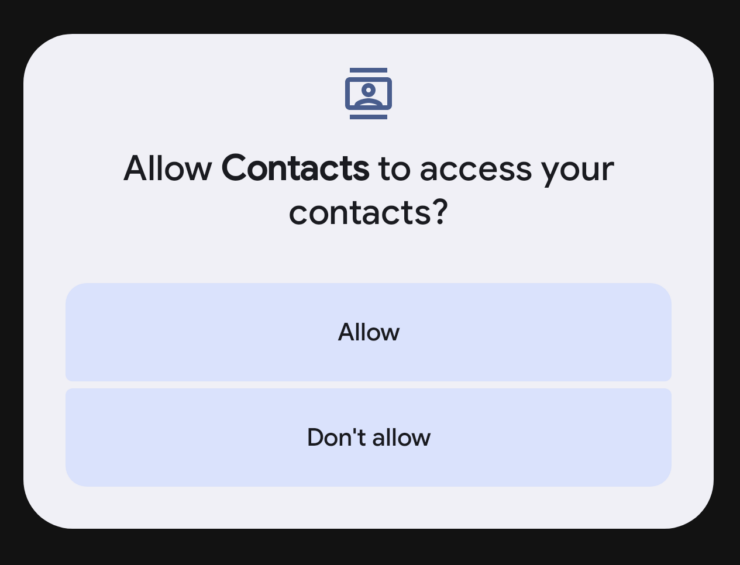
As seen from the screenshot, it appears that this app is requesting for such permissions, which could equate to granting hackers remote access. The first two pointers indicate that content onscreen will be monitored remotely, regardless if you are on the app itself.
Other redundant permissions would include access to the microphone and camera. Location requests might be relevant according to the usage scenario of the application in question.
Users would have to think about why they would be granting these permissions in the first place. An app which claims to provide content or promotion does not need to know what you are doing on your phone.
The source of the application matters. Broadly speaking, users are advised to only download apps from authorised app stores. Anything beyond these stores should be downloaded with discretion.
- Is the application downloaded for internal development purposes
- What is the purpose of the app – why are the permissions required
One-TIme-Passcodes (OTPs) should only be shared with those you trust – when absolutely necessary. Users are advised against sharing their codes with strangers.
What to do if you’ve been hacked?
Users who find themselves compromised should immediately exercise the following measures:
- Switch your phone to airplane mode
- Contact the relevant financial institutions to freeze your account
- Gather evidence (screenshot of the app icon)
- Factory reset your phone – when it is appropriate to do so (you might want to retrieve your personal information)
🤓 Like what you read?
Stay updated by following us on Telegram, Facebook, Instagram or on our YouTube channel.